I’m thinking it would involve that Hellfire Flying Ginsu.What would DJT do?

-
Be sure to read this post! Beware of scammers. https://www.indianagunowners.com/threads/classifieds-new-online-payment-guidelines-rules-paypal-venmo-zelle-etc.511734/
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber attack shuts down U.S. fuel pipeline ‘jugular,’ Biden briefed
- Thread starter bwframe
- Start date
The #1 community for Gun Owners in Indiana
Member Benefits:
Fewer Ads! Discuss all aspects of firearm ownership Discuss anti-gun legislation Buy, sell, and trade in the classified section Chat with Local gun shops, ranges, trainers & other businesses Discover free outdoor shooting areas View up to date on firearm-related events Share photos & video with other members ...and so much more!
Member Benefits:
Energy independence to gasoline shortages in (4) months, Way to go Joe !
If you need me to do your homework for you all you have to do is ask. No need to be a jerk.This seems to be a theme with several of your posts this week.
Bitcoin bounced between 3k-9k during 2019. this study published by Oxford university puts 46% of the transaction volume (76 billion) as illicit activities.
that’s a pretty strong correlation between criminal activity and the start of the massive rise in value of Bitcoin.
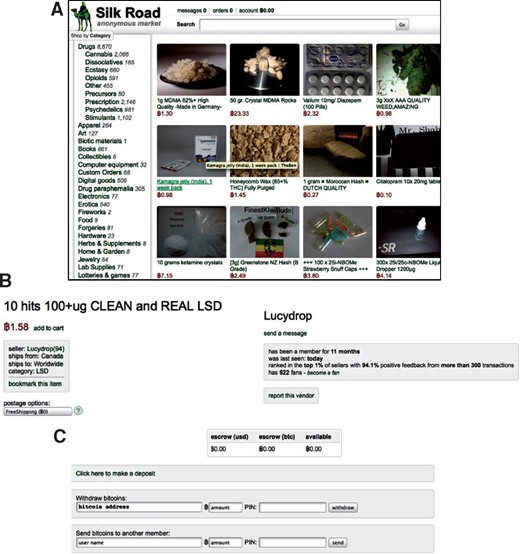
Sex, Drugs, and Bitcoin: How Much Illegal Activity Is Financed through Cryptocurrencies?
Abstract. Cryptocurrencies are among the largest unregulated markets in the world. We find that approximately one-quarter of bitcoin users are involved in illeg
Reports coming out that colonial paid the ransom.
I wonder if they had insurance.
What would DJT do?

What would Teddy Roosevelt do?
Reports coming out that colonial paid the ransom.
Say hello to an avalanche of these kind of attacks targeting infrastructure.
flyingsquirrel
Master
I have no proof but I believe the fuel crisis was not helped with the media throwing fuel on the fire. DEFUND THE MEDIA!
The avalanche started a few years ago. They are already attacking pretty much all businesses. This payoff is only one of the latest, the vast majority of which you never hear about. Compared to their lost revenue being shutdown, I imagine it was a small price to pay. Of course it would have been better if they had been better prepared.Say hello to an avalanche of these kind of attacks targeting infrastructure.
Yup, this has been going on for awhile. Jasper Engines was hit last year, and one of our main foam suppliers, Carpenter, was just hit a few months ago.The avalanche started a few years ago. They are already attacking pretty much all businesses. This payoff is only one of the latest, the vast majority of which you never hear about. Compared to their lost revenue being shutdown, I imagine it was a small price to pay. Of course it would have been better if they had been better prepared.
Ease up mad man. There was no "JerK" response here as I agree. Now call me a "JERK" OK.If you need me to do your homework for you all you have to do is ask. No need to be a jerk.
Bitcoin bounced between 3k-9k during 2019. this study published by Oxford university puts 46% of the transaction volume (76 billion) as illicit activities.
that’s a pretty strong correlation between criminal activity and the start of the massive rise in value of Bitcoin.

Sex, Drugs, and Bitcoin: How Much Illegal Activity Is Financed through Cryptocurrencies?
Abstract. Cryptocurrencies are among the largest unregulated markets in the world. We find that approximately one-quarter of bitcoin users are involved in illegacademic.oup.com
It is the tone of your posts. Know that we are all unhappy/angry. All of us not just you.
Follow the money?What would Teddy Roosevelt do?

Throwing money at bad behavior leads to more bad behavior. On the other hand: well planned, well coordinated, well executed violence solves problems.
Every normal man must be tempted, at times, to spit on his hands, hoist the black flag, and begin slitting throats.
-Mencken
The equipment itself doesn't necessarily need (or have) public IP addresses. However, if it is to be remotely operated and monitored, it needs to be on a network. That network needs to be accessible via a system that is available from a public space, even if that is simply a "jump box" with dual network cards. If you can legitimately tunnel down to the equipment to control it, the same path can be used to hack the equipment.
Since this was a ransomware attack, not a controls attack, the equipment itself may very well be untouched, but they want to be certain that the overall controlling server is clean before resuming operations to ensure they don't end up with an environmental disaster due to an over pressure, etc. They did say "we proactively took certain systems offline to contain the threat".
--Rick
So, the hackers put malicious software on critical infrastructure systems and lock them up or encrypt files, or whatever. The utility pays the "ransom," so the hackers log into their malicious software to instruct it to release the system files. But the malicious software is still there, and the hackers now know they can get an easy payday unless the utility replaces all of their hardware and software (I wonder if they use any of those Chinese routers with a backdoor?).
They used to operate it manually, and to get it running again they operated it manually.
More convenience = less security.
Not exactly. The bad guys give them a key that unlocks the files. The hardware doesn't need to replaced, and the software may or may not. That depends upon their level of trust and the malware installed. I would probably make new servers and bring the data to the new servers after scanning it for malicious software.So, the hackers put malicious software on critical infrastructure systems and lock them up or encrypt files, or whatever. The utility pays the "ransom," so the hackers log into their malicious software to instruct it to release the system files. But the malicious software is still there, and the hackers now know they can get an easy payday unless the utility replaces all of their hardware and software (I wonder if they use any of those Chinese routers with a backdoor?).
They used to operate it manually, and to get it running again they operated it manually.
More convenience = less security.
This had nothing to do with Chinese router backdoors. Odds are that an employee did something stupid or they didn't apply a patch to a vulnerable system to initially let the bad guys in.
Or (as I often suspect) it was an inside job or they bribed an employee. Money does change peoples level of morality/honor/honesty.Not exactly. The bad guys give them a key that unlocks the files. The hardware doesn't need to replaced, and the software may or may not. That depends upon their level of trust and the malware installed. I would probably make new servers and bring the data to the new servers after scanning it for malicious software.
This had nothing to do with Chinese router backdoors. Odds are that an employee did something stupid or they didn't apply a patch to a vulnerable system to initially let the bad guys in.
eldirector
Grandmaster
I've witnessed a few of these "attacks". Usually starts with a successful phishing, or someone on your network with really terrible security. The attackers then remote in, find something of interest (a large database, large file system, or something else critical) and encrypt it. YOU lose access, and it can only be restored with the decryption key - for a price.
Importantly, the attackers do NOT take any data. That kind of breach (and theft of corporate data) is governed by different international laws, and isn't worth the risk. They just want enough pain that you pay up, but not so much you call the CIA/FBI, and not so much you just grab new hardware and restore from backup.
There are thousands of these per year, easily, across the US. We don't hear about them. Either the ransom is paid, or the hardware is just wiped and restored from backup.
Importantly, the attackers do NOT take any data. That kind of breach (and theft of corporate data) is governed by different international laws, and isn't worth the risk. They just want enough pain that you pay up, but not so much you call the CIA/FBI, and not so much you just grab new hardware and restore from backup.
There are thousands of these per year, easily, across the US. We don't hear about them. Either the ransom is paid, or the hardware is just wiped and restored from backup.
Not likely with a ransomware attack. That would go back to plain old fashioned theft.Or (as I often suspect) it was an inside job or they bribed an employee. Money does change peoples level of morality/honor/honesty.
You have one point wrong. The DO take data. One of their threats to get the ransom is that they will publish data online if not paid. These guys apparently got about 100Gb worth.I've witnessed a few of these "attacks". Usually starts with a successful phishing, or someone on your network with really terrible security. The attackers then remote in, find something of interest (a large database, large file system, or something else critical) and encrypt it. YOU lose access, and it can only be restored with the decryption key - for a price.
Importantly, the attackers do NOT take any data. That kind of breach (and theft of corporate data) is governed by different international laws, and isn't worth the risk. They just want enough pain that you pay up, but not so much you call the CIA/FBI, and not so much you just grab new hardware and restore from backup.
There are thousands of these per year, easily, across the US. We don't hear about them. Either the ransom is paid, or the hardware is just wiped and restored from backup.
Latest posts
-
-
The Effect of "Abortion Rights" on the Political Landscape
- Latest: AndreusMaximus
-
Members online
- Andyccw
- WebSnyper
- Mr. Habib
- jwamplerusa
- Hoosierdood
- resdep
- TR1032
- magic man
- Nazgul
- BeDome
- Judamonster
- bobzilla
- SEMI-AK
- TheGrumpyGuy
- Rescue912
- HoughMade
- spencer rifle
- Seedogg
- AndreusMaximus
- mondoreli
- ISP 5353
- Cavman
- Jarvitron
- BugI02
- melensdad
- Kenjiboijoi
- DCR
- cobber
- 2tonic
- jsharmon7
- zoglog
- dieselrealtor
- sescbo
- rkwhyte2
- Ingomike
- STEEL CORE
- bgcatty
- SheepDog4Life
- firefighterjohn
- billmyn
- warren5421
- A. Ramon
- actaeon277
- Dr.Midnight
- ZurokSlayer7X9
- johnb62
- lafrad
- Snapdragon
- Ford Truck
- JRR85
Total: 1,552 (members: 233, guests: 1,319)




